What is Secure Multiparty Computation?
Secure multiparty computation (MPC / SMPC) is a cryptographic protocol that distributes a computation across multiple parties where no individual party can see the other parties’ data.
Secure multiparty computation protocols can enable data scientists and analysts to compliantly, securely, and privately compute on distributed data without ever exposing or moving it.
Inpher’s Secret Computing® technology encompasses two complementary encryption in-use techniques: Secure Multiparty Computation (MPC / SMPC) and Fully Homomorphic Encryption (FHE). Watch the video below for a simple example of how secure multiparty computation works in action!
Secure Multiparty Computation: An Example
Salary “sharing” without sharing.
An illustrative MPC example.
Situation: Three coworkers —Allie, Brian, and Caroline— want to compute their average salary.
Complication: Each person does not want to reveal their individual salary information to each other or a trusted third-party during the computation.
Resolution: Allie, Brian, and Caroline use a secure multiparty computation protocol to calculate the average without ever revealing their private salary information during the process. The secure multiparty computation protocol leverages a well-established cryptographic concept called additive secret sharing, which refers to the division of a secret and its distribution among a group of independent, willing participants.
How It Works:
Disclaimer: The purpose of the following example is to illustrate the high-level concept that underlies secure multiparty computation — not its mathematical foundations. If you’re interested in the math that ensures cryptographic security, check out our Journal of Cryptology paper.
In our example, say Allie’s salary is $100k. In additive secret sharing, $100k is split into three randomly-generated pieces (or “secret shares”): $20k, $30k, and $50k for example. Secret sharing is a way to encrypt data while it is in use. Allie keeps one of these secret shares ($50k) for herself, and distributes one secret share to each Brian ($30k) and Caroline ($20k). Brian and Caroline also secret-share their salaries while following the same process (see table below for example secret shares). When the secret sharing is completed, each person holds three secret shares: one from Allie’s salary, one from Brian’s, and one from Caroline’s.
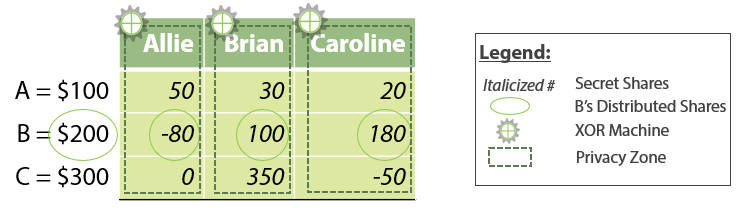
Note that when the three salaries are secret shared across the participants (as shown above), they know nothing about each other’s salaries. Each secret share provides no useful information on its own; a secret share, after all, is just a piece of incomplete information about the initial secret value from which it was derived.
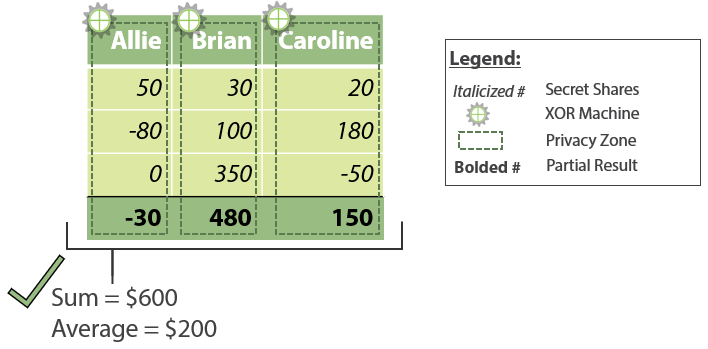
However, secret shares provide valuable information when added up (hence, the “additive” in additive secret sharing). Each participant locally sums their secret shares to calculate a partial result; in our example, each partial result is one third of the necessary information to calculate the final answer. The partial results are then recombined, summing the complete set of secret shares previously distributed. As you can see below, the recombined sum divided by the number of participants yields our answer; Allie, Brian, and Caroline’s average salary is $200k.
Something to remember: Secure multiparty computation is often assumed to require the participation of multiple organizations. This, however, is not a requirement. What is required, on the other hand, are multiple privacy zones, which refers to two or more domains with different sets of privacy restrictions. Multiple privacy zones exist across multiple organizations, but they also can exist within a single organization across teams, departments, and/or jurisdictions.
Benefits of Secure Multiparty Computation

-
Commercially-ready: Secure multiparty computation is no longer a data scientist’s dream; it is a proven reality. Today, customers are using Secret Computing® to better detect financial fraud, aggregate model features across private datasets, better predict heart disease — and much more. Check out our Use Cases pages to learn about more ways data scientists are using secure multiparty computation in production today.
-
No trusted third-parties see the data: It is no longer necessary to trust a third-party to keep data safe and broker exchanges. Clients never transfer data outside their internal firewalls.
-
Eliminates tradeoff between data usability and data privacy: There is no need to mask or drop any features in order to preserve the privacy of data. All features may be used in an analysis, without compromising privacy.
-
GDPR and sovereign data privacy compliance: Inpher’s secure multiparty computation solution meets and exceeds requirements for cross-border data transfer (because the data never moves).
-
High accuracy and precision: Results meet and exceed client requirements for accuracy and precision.
-
Quantum-safe: Data is said to be encrypted in-use because it is broken up and distributed across players (or “secret shared”) during the computation, which makes it safe against quantum attacks.
Limitations of Secure Multiparty Computation
-
Computational overhead: Random numbers must be generated in order to ensure the security of the computation (not discussed in the illustrative example above). The random number generation requires computational overhead, which can slow down run time.
-
High communication costs between players: Secret sharing involves communication and connectivity between all participants, which leads to higher communication costs as compared to plaintext compute.
Secure Multiparty Computation is ready
Inpher’s XOR Secret Computing® Engine leverages secure multiparty computation and solves real-world business problems today. Visit our Use Cases pages and contact us today to learn more!

