In this blog we discuss the seven foundational principles of privacy by design. While privacy by design has now been formalized in data protection laws globally–from the EU to the U.S., Europe, and Australia–examining those original principles offers many insights.
First introduced in 1995, privacy by design evolved alongside privacy-enhancing technologies (PETs) and is intended to address the broader systems and processes in which PETs operate. Aiming to provide a universal framework, privacy by design can apply to information technologies, organizational practices, physical design, or networked information ecosystems.
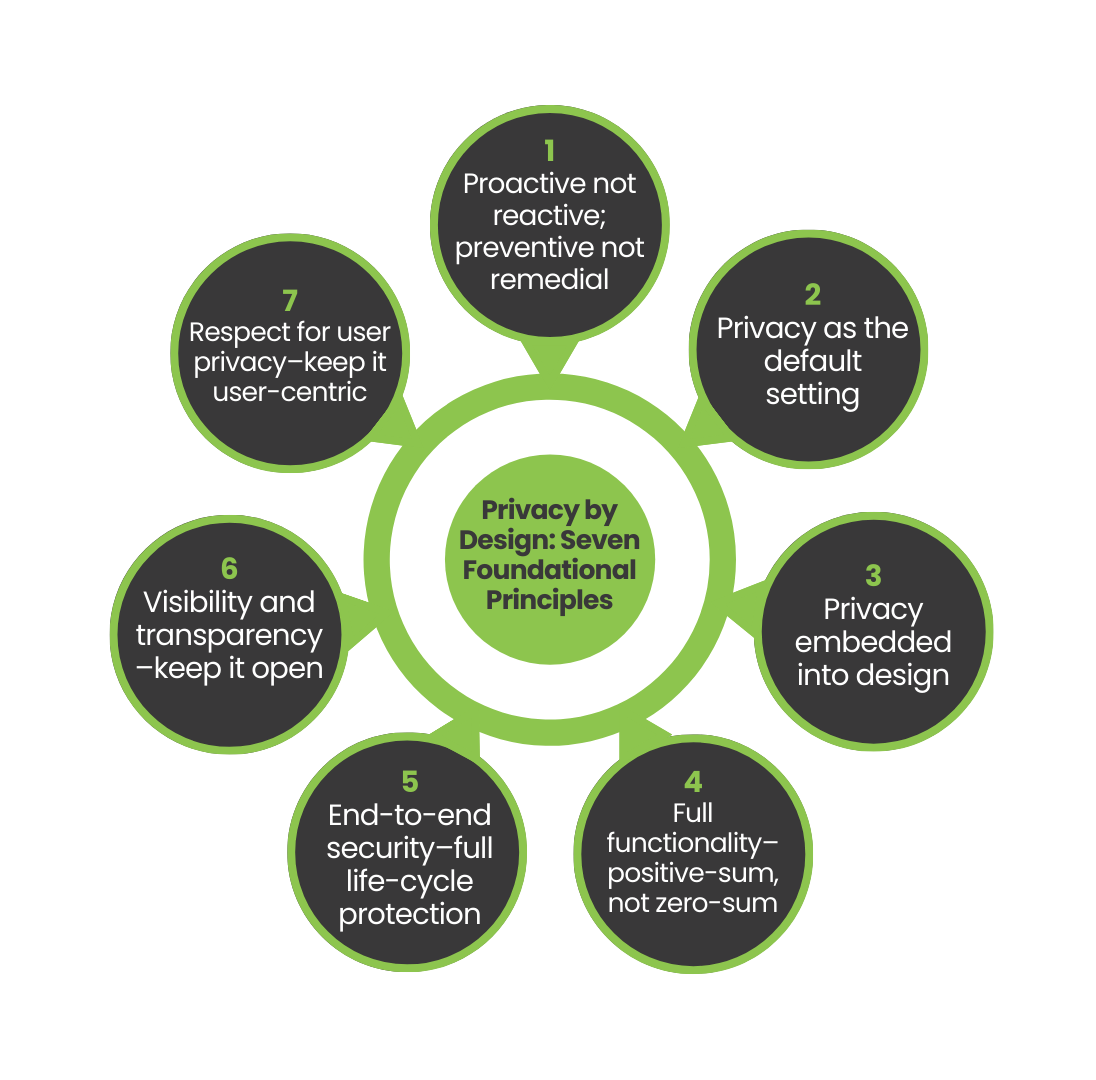
The Seven Foundational Principles
Privacy by design is based on seven foundational principles.
-
Proactive not reactive; preventive not remedial
Privacy by design is premised on the benefits of proactively adopting strong privacy practices and integrating privacy into all organizational priorities, project objectives, design processes, and planning operations. Privacy by design focuses on preventing privacy infractions, not resolving them after they have taken place. This involves a strong commitment at all levels of an organization to uphold high privacy standards, possibly even higher than the standards set out by global laws and regulations.
-
Privacy as the default setting
With privacy by design, personal data are automatically protected in any given IT system or business practice: privacy is built into the system by default. The collection, use, retention, and disclosure of personal information should be limited to the purposes the individual has consented to, unless otherwise required by law. The default setting should always be the most privacy protective. The EU’s General Data Protection Regulation (GDPR) includes data protection by default in Article 25.
-
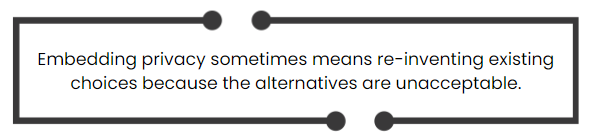
Privacy embedded into design
Privacy must be embedded into technologies, operations, and information architectures from the beginning. It should not be an add-on. The approach should rely on accepted standards and frameworks that can be externally reviewed and audited. Ideally, detailed privacy and risk assessments should be conducted and privacy impacts should be demonstrably minimized.
-
Full functionality–positive-sum, not zero-sum
Privacy by design aims to achieve positive-sum, “win-win” outcomes. In a zero-sum view, privacy might be placed in competition with other valid interests, design objectives, and technical capabilities. Instead, legitimate non-privacy objectives should be embraced and accommodated. Those who meet all objectives in an innovative, positive-sum manner can be considered global privacy leaders.

-
End-to-end security–full life-cycle protection
There is no privacy without strong security. Having been embedded before any data were collected, privacy by design applies throughout the entire life cycle of that data: all data are securely retained, then securely destroyed at the end of the process. In this way, privacy by design ensures secure life-cycle information management.
-
Visibility and transparency–keep it open
Trust but verify! Whatever the business practice or technology involved, stakeholders should feel confident that it conforms to the stated promises and objectives, subject to independent verification. Its component parts and operations must remain visible and transparent to users and providers alike. For auditing purposes, the following three Fair Information Practices (FIPs) can be emphasized:
- Accountability. It should be clear who is responsible for privacy-related policies and procedures.
- Openness. People should have easy access to information about how personal information is managed.
- Compliance. Compliance should be effectively monitored, evaluated, and verified. People should be able to easily report violations.

-
Respect for user privacy–keep it user-centric
Keep it user-centric! Broadly speaking, human-machine interfaces should be designed to be human-centered and user-friendly, so that individuals can make informed privacy decisions. After all, users are the ones who care the most about their own personal data. Giving data subjects the power to actively manage their own data is perhaps the most effective check against abuses and misuses of privacy and personal data.
To learn more about how Inpher supports privacy by design and the win-win outcomes it promotes, visit our website.

